
Cybersecurity needs Design: Reflections on my first two months at a cyber security startup
Hi, I'm Hal, a product designer at Flatt Security. This October, I transitioned to Flatt Security after working at freee for eight years.
Flatt Security is a cybersecurity startup with talented security researchers who have reported vulnerabilities to leading companies such as Google, Cloudflare, GitHub, Salesforce, and Microsoft.
When I joined, there were no designers and product managers in the product team. My mission was not only to design products but also to define and demonstrate how design can drive value in such an environment.
At the time, my knowledge of cybersecurity was almost zero. On top of that, I was suddenly surrounded by engineers discussing complex security jargons in English where I didn’t even know what I didn’t know. Despite this, I had to jump right in, participating in business discussions, identifying areas critical for growth, and taking action to design for problem solving.
What I Did in My First 2 Months
Reflecting on my first two months, here’s what I accomplished:
- Participated in over 15 business meetings.
- Conducted usability tests: 5 externally and 4 internally.
- Facilitated persona creation, involving sales, development teams, CTO, CEO, and CCO to align product direction.
- Demonstrated our product to nearly 30 clients at an IT exhibition at Makuhari Messe.
- Redesigned three features based on customer feedbacks.
- Implemented more than five UI improvements.
If this sounds like a lot for two months, I'd like you to know I didn’t do it all alone. Instead, I let go of many things and focused on the essentials.
3 Things What I Let Go of when I joined a cybersecurity startup
- Don’t try to design everything.
- Don’t design alone.
- Don’t create formal user research process.
1. Don’t try to design everything, insteaad focus on the Essentials
When you join as the first product designer, expectations from your fellow are incredibly high, and you can see countless areas for improvement. As a result, your "to-do list" can quickly grow overwhelming within just a few weeks.
But you should not do all your to-do lists. Instead, you should focuse on identifying what is truly essential by asking two questions:
- What’s the biggest blocker for the business?
- How can design contribute?
When unsure, I sought insights from key stakeholders by attending meetings, showcasing demos, and having discussions with team members like the CTO and Biz Dev colleagues. Based on these interactions, I prioritized projects that contributed to business growth, some of which became features highly praised in client discussions.
2. Don’t design alone, instead design together
Design isn’t only for designer. At Flatt Security, where cyber security experts develop products for engineers, I realized the value of co-designing with the team.
It's crucial to involve the entire company and design collaboratively. As a designer, I’ve continued learning about engineering to understand the domain better, even rebuilding my portfolio(this site) using Next.js and p5.js to expand my knowledge.
That said, cybersecurity is a challenging field, even for seasoned engineers. If I could become as knowledgeable as the development team in this area, I might as well call myself a security engineer.
However, one of my key missions here is to define and demonstrate how design can drive maximum value in this environment. To ensure design thrives in the complex field of cybersecurity, it’s essential to create an environment where enabling engineers design together
Using the “N1 Sheet” to align with engineers
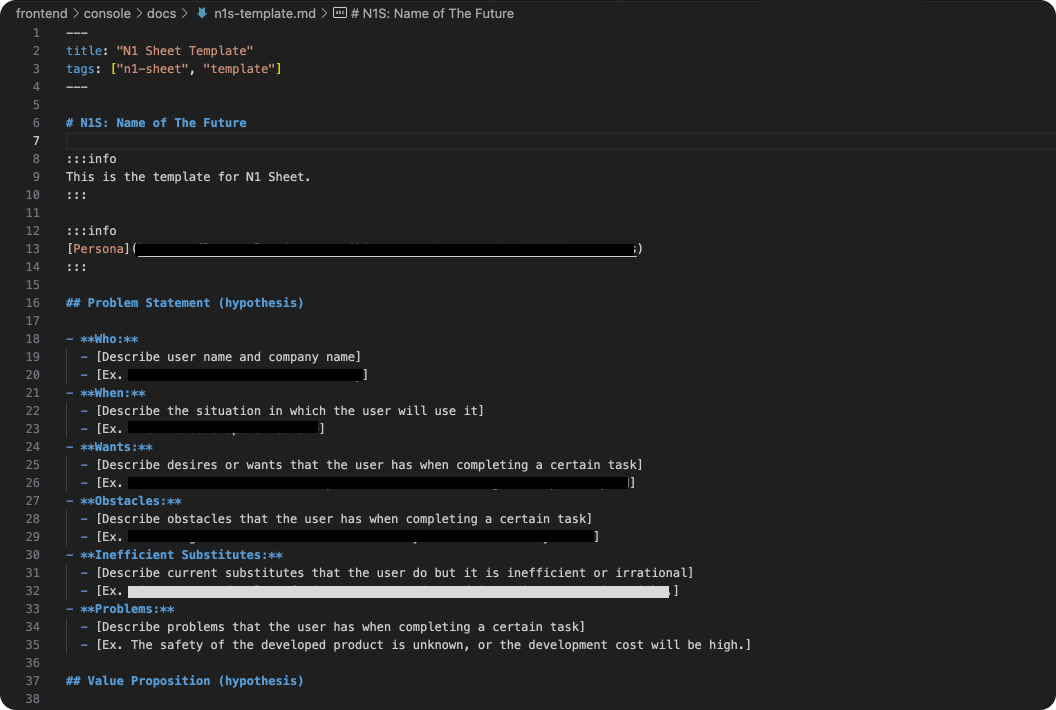
To foster collaboration, I introduced the N1 Sheet, inspired by SmartBank’s article. This sheet helps engineers clarify user needs, pain points, and value propositions, and we store it directly in the codebase to keep it accessible.
Think N1 Sheet is a template a design document to define Why and What of a new product or feature.
After an engineer fills out the N1 Sheet, I:
- Engage them in discussions to refine the value we want to deliver.
- Identify assumptions and verified facts, updating the sheet based on feedback or interviews.
- Use the refined value proposition to create user scenarios and share the resulting UI design process with the team.
This collaborative approach helps build trust and understanding while ensuring designs align with customer needs.
Persona creation involving the entire company
 Within two weeks of joining, I initiated persona creation by involving the entire company, including the CEO, CTO, sales, engineers, and security experts.
Within two weeks of joining, I initiated persona creation by involving the entire company, including the CEO, CTO, sales, engineers, and security experts.
Instead of leading with my limited knowledge, I facilitated persona workshop, empowering those who interact with customers to contribute their insights. This collective effort aligned our focus on who we’re designing for.
3. Don’t create formal user research process, instead sneak into opportunities to meet customers
 At freee, I experienced a strong user research culture. While I wanted to replicate that, limited resources and budget in a startup made it challenging to set up formal research processes. Instead, I attended as many sales meetings as possible during my first month.
At freee, I experienced a strong user research culture. While I wanted to replicate that, limited resources and budget in a startup made it challenging to set up formal research processes. Instead, I attended as many sales meetings as possible during my first month.
I also participated in the Japan IT Week exhibition, doing demo our product to over 30 attendees in two days. These interactions helped me understand the business landscape and identify critical areas for improvement, even without a formal research setup.
If you’re struggling to find research opportunities as the first designer, consider “sneaking into” customer-facing situations like business meetings or exhibitions.
Cybersecurity needs design
In today’s world, where security incidents like data breaches are increasing, the importance of cybersecurity cannot be overstated. However, even technical experts like software engineers find this field complex and fraught with risk.
That’s why I believe design is essential in cybersecurity. My mission is to create an environment where all members of Flatt Security can “design”, as cyber security specialist gathers, rather than I design alone. By embedding design into our processes, I aim to make cybersecurity more accessible and effective for everyone.